WordPress Security Issues can pose significant risks to websites if not addressed properly. One common vulnerability includes outdated plugins and themes, which hackers often exploit. Weak passwords and a lack of two-factor authentication further expose websites to unauthorized access. Additionally, improper file permissions and unprotected admin areas make sites more susceptible to breaches. To mitigate WordPress Security Issues, regularly update your WordPress core, themes, and plugins. Implement robust security measures such as firewalls and malware scanners. Protect your site with secure hosting and SSL certificates to ensure data encryption. By addressing WordPress Security Issues, you safeguard your website and user data effectively.
In this article, we’ll explore 16 critical WordPress security issues you should be aware of and provide tips to help you safeguard your site.
1. Outdated Core Software
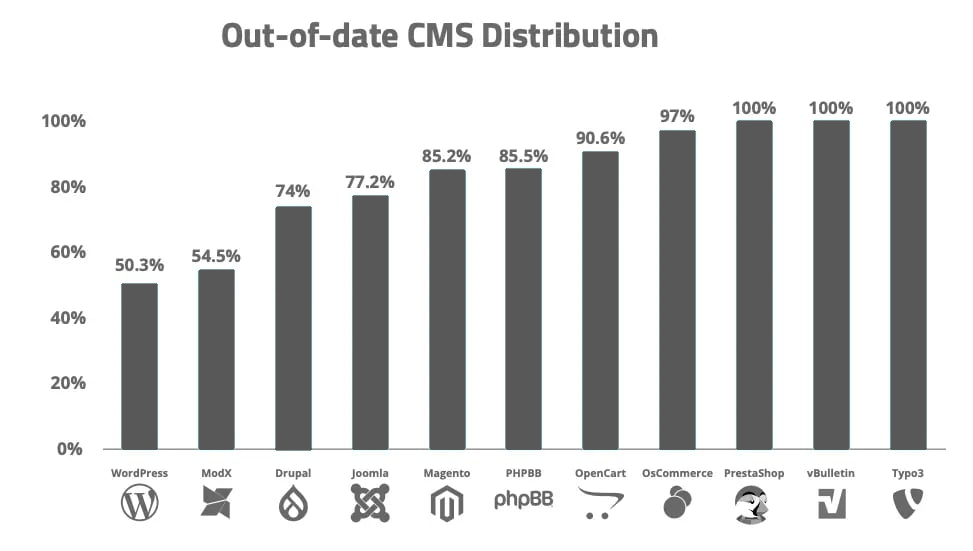
One of the most common and dangerous WordPress security vulnerabilities arises from outdated core software. WordPress consistently releases updates not only to introduce new features and improve the overall performance of the platform but also to patch known security loopholes.
These patches address vulnerabilities that, if left unpatched, can be exploited by cybercriminals. Regular updates are vital to maintaining the security integrity of your site, as they help protect against emerging threats that could compromise the system.
However, many website administrators often overlook or delay these updates, believing that updating the core software could disrupt their website or break their existing themes or plugins.
This hesitation can result in prolonged periods where the site is vulnerable to known exploits. Even though keeping WordPress up to date is a simple task, failure to do so leaves your site exposed to potential attacks.
Why it’s a problem:
The outdated core software is essentially an open invitation for hackers who are familiar with the vulnerabilities present in earlier versions.
Attackers can exploit these known weaknesses to infiltrate your site, steal data, or even take over the entire site. Once inside, they can inject malicious code, deface your website, or use your server as a launchpad for further attacks.
Since the details of the vulnerabilities addressed by each update are often publicly available, it becomes easier for cybercriminals to target websites that are still running older versions of WordPress.
How to prevent it:
To avoid the risks associated with outdated software, always update your WordPress version as soon as updates are available. You can enable automatic updates to streamline this process and ensure that your site is always running the latest, most secure version of WordPress.
Additionally, opting for managed WordPress hosting services can be a great solution, as these providers typically handle updates automatically, ensuring that your site remains protected without requiring manual intervention.
Keep a habit of regularly checking for updates, especially if you manage multiple websites.
2. Outdated Themes and Plugins
Similarly, outdated themes and plugins pose a significant threat to WordPress security. Themes and plugins are essential for customizing and extending the functionality of WordPress websites, enabling site owners to add features like galleries, contact forms, and e-commerce capabilities.
However, if they are not regularly updated, they can introduce vulnerabilities. Many third-party developers create plugins and themes, which means that security standards can vary.
Hackers specifically target outdated or poorly coded plugins and themes to exploit known vulnerabilities.
Why it’s a problem:
Cybercriminals often exploit vulnerabilities in outdated themes and plugins. Once they identify a vulnerability, attackers can gain unauthorized access to your site, inject malicious code, steal data, or even take complete control of your website.
This could result in significant damage to your site’s reputation, data breaches, and potential loss of revenue.
Furthermore, outdated plugins and themes may no longer be compatible with newer versions of WordPress, which can lead to site functionality issues or breakages.
How to prevent it:
- Regularly update all installed themes and plugins. Keeping your themes and plugins updated ensures that any newly discovered security flaws are patched, reducing the risk of exploitation.
- Remove any unused or unnecessary plugins and themes. Unused components still pose a risk because they may be outdated or abandoned by their developers. Deleting them minimizes your site’s potential attack surface.
- Download themes and plugins only from trusted sources, like the official WordPress repository, reputable developers, or well-known third-party marketplaces. Avoid downloading free or pirated themes from unreliable sources, as they may contain malicious code.
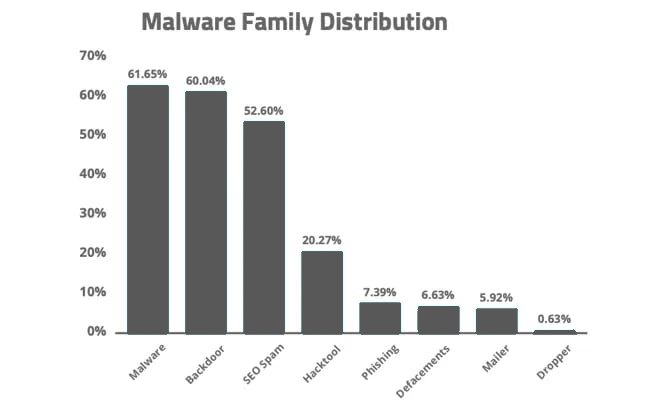
3. Malware
Malware refers to any malicious software designed to harm, exploit, or compromise your website. This term encompasses a variety of harmful programs, including viruses, worms, Trojans, ransomware, and more.
Once malware infiltrates your website, it can steal sensitive data, display unwanted advertisements, manipulate your content, or even hijack the site entirely for nefarious purposes.
In extreme cases, malware can lead to the complete shutdown of your website, resulting in significant financial losses and reputational damage.
Why it’s a problem:
Malware can cause data breaches, deface your website, and lead to the theft of sensitive financial or personal information. A successful malware attack can compromise customer trust, affecting your business’s credibility.
Additionally, in some cases, your website may be blacklisted by search engines if it’s found to host malware, which significantly reduces traffic and visibility, making it even harder for potential customers to find you online.
Once blacklisted, it can take considerable time and effort to rectify the issue, further impacting your site’s performance.
How to prevent it:
To safeguard your website against malware, it’s crucial to install security plugins like Wordfence which actively scan for malicious code and vulnerabilities. Regularly backing up your site is another essential practice, ensuring that you can restore it quickly in case of an infection.
Furthermore, ensure your site’s hosting provider offers robust malware protection services, such as real-time scanning and threat detection, to help prevent any potential breaches from occurring in the first place.
By taking these proactive measures, you can significantly reduce the risk of malware infiltrating your website and protect your valuable assets.
4. Credit Card Skimming
Credit card skimming is a type of cyberattack in which hackers inject malicious code into your site to capture credit card details during online transactions.
This practice is particularly dangerous for e-commerce websites that rely on payment processing platforms like WooCommerce or similar plugins.
Once attackers successfully implant this code, they can harvest sensitive financial information from unsuspecting customers as they make purchases. The repercussions can be severe, affecting both your business’s reputation and your customers’ financial security.
Why it’s a problem:
If a hacker gains access to your customer’s credit card information, it could lead to fraudulent purchases, identity theft, and substantial legal consequences for your business.
Furthermore, the trust of your customers can be severely undermined if they believe their financial data is not secure on your site. This breach of trust can result in lost sales, a tarnished reputation, and ongoing challenges in regaining customer confidence.
How to prevent it:
To safeguard against credit card skimming, use a secure, PCI-compliant payment gateway that encrypts sensitive data during transactions. Regularly scan your site for malicious scripts that could indicate an ongoing attack.
It’s also crucial to implement strong authentication methods, such as two-factor authentication (2FA), for admin access. By doing so, you add layer of security that makes it significantly harder for unauthorized users to gain access to your site.
5. Unauthorized Logins
Weak or easily guessable passwords make unauthorized logins a persistent issue for WordPress websites. Attackers often employ brute force attacks, where they use automated tools to repeatedly attempt to guess login credentials until they succeed.
These attacks can occur on a large scale, targeting multiple sites simultaneously, and can result in unauthorized access to sensitive information.
Why it’s a problem:
Once a hacker gains access to your admin account, they can change passwords, steal valuable data, or infect your website with malware, leading to potential downtime and loss of sensitive information.
Additionally, the consequences of a security breach can extend beyond immediate financial losses, affecting your business’s reputation and customer trust in the long run.
An infected site can also lead to your website being blacklisted by search engines, further compounding the problem.
How to prevent it:
To mitigate the risks associated with unauthorized logins, use strong, unique passwords that include a combination of letters, numbers, and special characters.
Implementing two-factor authentication (2FA) adds an extra layer of security, making it much more challenging for hackers to gain access, even if they manage to guess a password.
Furthermore, limit the number of login attempts to thwart brute force attacks, ensuring that after a certain number of failed attempts, the account gets temporarily locked or flagged for review. This simple step can significantly enhance your site’s overall security posture.
6. Undefined User Roles
In WordPress, different users are assigned different roles (such as Administrator, Editor, Author, and Subscriber), each with varying levels of access to the site’s features and functionalities.
Failing to properly define these roles can lead to unauthorized actions by users who have more permissions than necessary. This misconfiguration can result in serious security vulnerabilities that could be exploited by malicious actors.
Why it’s a problem:
Granting higher levels of access than needed increases the risk of accidental or malicious actions, such as the deletion of important files, changes to critical website settings, or the installation of unauthorized plugins.
Such actions could compromise the integrity of your website and potentially lead to data loss or unauthorized access.
How to prevent it:
To mitigate these risks, assign user roles carefully based on the specific tasks and responsibilities each individual will perform on the site. It is essential to ensure that users have the minimum necessary permissions required to complete their duties effectively.
Additionally, regularly review user roles and permissions to ensure they align with your organization’s security policies and the evolving needs of your team.
This proactive approach can help identify any potential security risks associated with misconfigured user roles, ultimately enhancing the overall security posture of your WordPress site.
7. Structured Query Language (SQL) Injections
SQL injections are among the most common and dangerous attack methods used against WordPress websites.
Attackers insert malicious SQL code into web forms, URLs, or input fields, tricking your site’s database into executing unauthorized commands, such as retrieving or deleting data. Even minor SQL vulnerabilities can lead to significant security issues if left unaddressed.
Why it’s a problem:
SQL injections can cause serious data breaches by allowing attackers to extract, modify, or delete sensitive information stored in your database, including customer data, passwords, and financial information.
How to prevent it:
- Use security plugins like Wordfence or Sucuri to detect and block SQL injection attempts.
- Implement prepared statements in your website’s code to sanitize user inputs before sending them to the database.
- Regularly audit your website for vulnerabilities and patch any outdated plugins or themes.
8. Search Engine Optimization (SEO) Spam
SEO spam involves hackers injecting spammy keywords, links, or content into your website to boost their own search engine rankings. This is often done covertly, with malicious links or content hidden within your code, making it hard to detect without thorough monitoring.
Why it’s a problem:
SEO spam can harm your site’s search engine rankings, reduce user trust, and damage your credibility. It can also redirect your visitors to unwanted or malicious websites, affecting your reputation.
How to prevent it:
- Regularly scan your website for unusual content, hidden links, or unauthorized changes.
- Use a web application firewall (WAF) to block known spammers and malicious bots.
- Keep your WordPress themes, plugins, and core files up-to-date to reduce vulnerabilities.
9. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) attacks occur when hackers inject malicious scripts into your website. These scripts run in the browsers of users who visit your site, potentially stealing personal information, session cookies, or redirecting users to malicious websites.
Why it’s a problem:
XSS attacks can allow attackers to impersonate legitimate users or administrators by hijacking session cookies. This can lead to identity theft, unauthorized access, and further exploitation of your site.
How to prevent it:
- Sanitize and validate all user input to block unauthorized script execution.
- Use a web application firewall (WAF) to filter malicious requests.
- Conduct regular security audits to identify XSS vulnerabilities early.
10. Denial-of-Service (DoS) Attacks
A Denial-of-Service (DoS) attack occurs when an attacker floods your server with excessive traffic, making your site inaccessible to legitimate users. Distributed DoS (DDoS) attacks are even harder to mitigate since they originate from multiple sources simultaneously, overwhelming your server’s capacity.
Why it’s a problem:
DoS attacks cause significant downtime, resulting in lost revenue, reduced user trust, and a damaged brand reputation. Extended outages can also affect your search engine rankings.
How to prevent it:
- Use a Content Delivery Network (CDN) like Cloudflare to absorb and mitigate DDoS attacks.
- Implement server-level security measures to block suspicious traffic patterns.
- Monitor traffic regularly to detect unusual spikes and respond quickly.
11. Phishing
Phishing attacks involve hackers sending fraudulent messages or setting up fake websites to trick users into revealing sensitive information, such as login credentials or payment details. These attacks often rely on social engineering, exploiting trust to gather confidential information.
Why it’s a problem:
Phishing can result in identity theft, unauthorized account access, and financial fraud. Hackers could gain access to admin accounts, giving them full control over your website.
How to prevent it:
- Educate users and staff on how to recognize phishing attempts and avoid suspicious links.
- Implement email authentication protocols like DKIM, DMARC, and SPF to prevent phishing emails.
- Enable two-factor authentication (2FA) to secure all user accounts.
12. Supply Chain Attacks
In supply chain attacks, hackers compromise third-party services, plugins, themes, or hosting providers your website relies on. These attacks allow malicious code to infiltrate your site indirectly through trusted sources.
Why it’s a problem:
Supply chain attacks are difficult to detect since they leverage legitimate software and services. This can introduce malware or backdoors, jeopardizing your site’s security without raising immediate red flags.
How to prevent it:
- Install themes and plugins only from reputable developers and marketplaces.
- Ensure third-party services follow strong security practices.
- Regularly monitor and audit third-party software for unusual activity.
13. Hotlinking
Hotlinking occurs when another website links directly to your images, videos, or other resources, using your server’s bandwidth without permission. This can increase your hosting costs and slow down your website’s performance.
Why it’s a problem:
Hotlinking drains your server resources, leading to slower load times for your visitors. It also allows other sites to use your content without attribution, which can affect your SEO and brand integrity.
How to prevent it:
- Use plugins or modify server settings to block hotlinking.
- Employ a CDN to offload resources and reduce bandwidth usage.
- Regularly monitor resource usage to identify unauthorized hotlinking.
14. Cross-Site Request Forgery (CSRF)
In Cross-Site Request Forgery (CSRF) attacks, hackers trick users into performing actions on your site without their consent. This is typically done by embedding malicious links or forms within emails or third-party websites.
Why it’s a problem:
CSRF attacks can enable attackers to change user settings, transfer funds, or manipulate site content—without the victim realizing it. These attacks can compromise both user accounts and administrative control.
How to prevent it:
- Use nonces (security tokens) in URLs and forms to validate legitimate requests.
- Deploy a web application firewall to block CSRF attempts.
- Educate users about the risks of clicking on suspicious links or forms.
15. Poor Web Hosting Security
The security of your hosting provider significantly impacts your website’s safety. Weak hosting security exposes your site to malware infections, unauthorized access, and slow performance, even if your internal security is robust.
Why it’s a problem:
If your hosting provider lacks strong security practices, your site is at risk of being compromised, regardless of the measures you’ve implemented. A breach at the hosting level can also affect other sites on the same server.
How to prevent it:
- Choose a hosting provider known for strong security protocols.
- Ensure your host offers features like daily backups, SSL certificates, and malware scanning.
- Consider VPS or dedicated hosting for enhanced security.
16.Weak or Unencrypted Connections (Lack of SSL)
Using HTTP instead of HTTPS leaves your site vulnerable to Man-in-the-Middle (MITM) attacks, where hackers intercept data between your server and users. Without SSL encryption, sensitive data, like login credentials and payment details, can be exposed during transmission.
Why it’s a problem:
Unencrypted data is susceptible to interception, leading to identity theft, financial losses, and damaged trust. Search engines like Google penalize non-HTTPS websites, negatively affecting your SEO and visibility.
How to prevent it:
- Implement SSL certificates to encrypt data between your site and users.
- Use HTTPS across all pages, not just login or payment pages.
- Regularly check your SSL configuration to ensure proper setup and functionality.
Final remarks
Securing your WordPress website is an ongoing process that requires constant vigilance, proactive measures, and the right tools.
By understanding the most common security threats—ranging from outdated software and plugins to sophisticated attacks like SQL injections and phishing—you can significantly reduce the risk of your site being compromised.
Implementing regular updates, strong passwords, SSL encryption, and trusted security plugins will go a long way in keeping your WordPress site safe from malicious actors.






